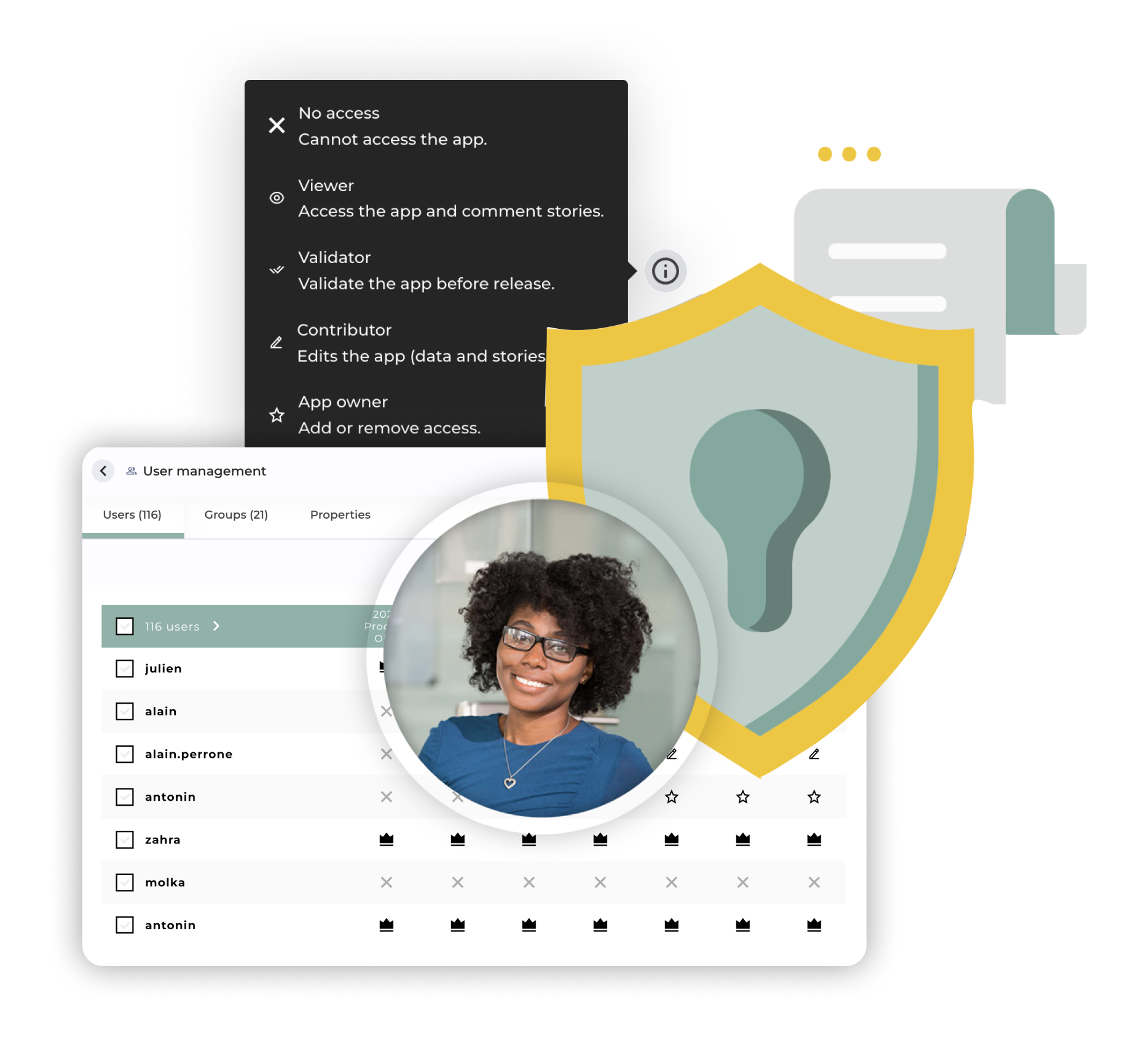
Effortless Permission Management
The most powerful user permission management systems are useless if they're so complex that no one can figure them out. Toucan's user management combines power with simplicity so that you can easily assign the right permissions to the right users without the headaches.
- Control access at app, role, user, or row levels
- Drive workflows and story flows via user configuration
- Configure default homepage dashboards by role or user
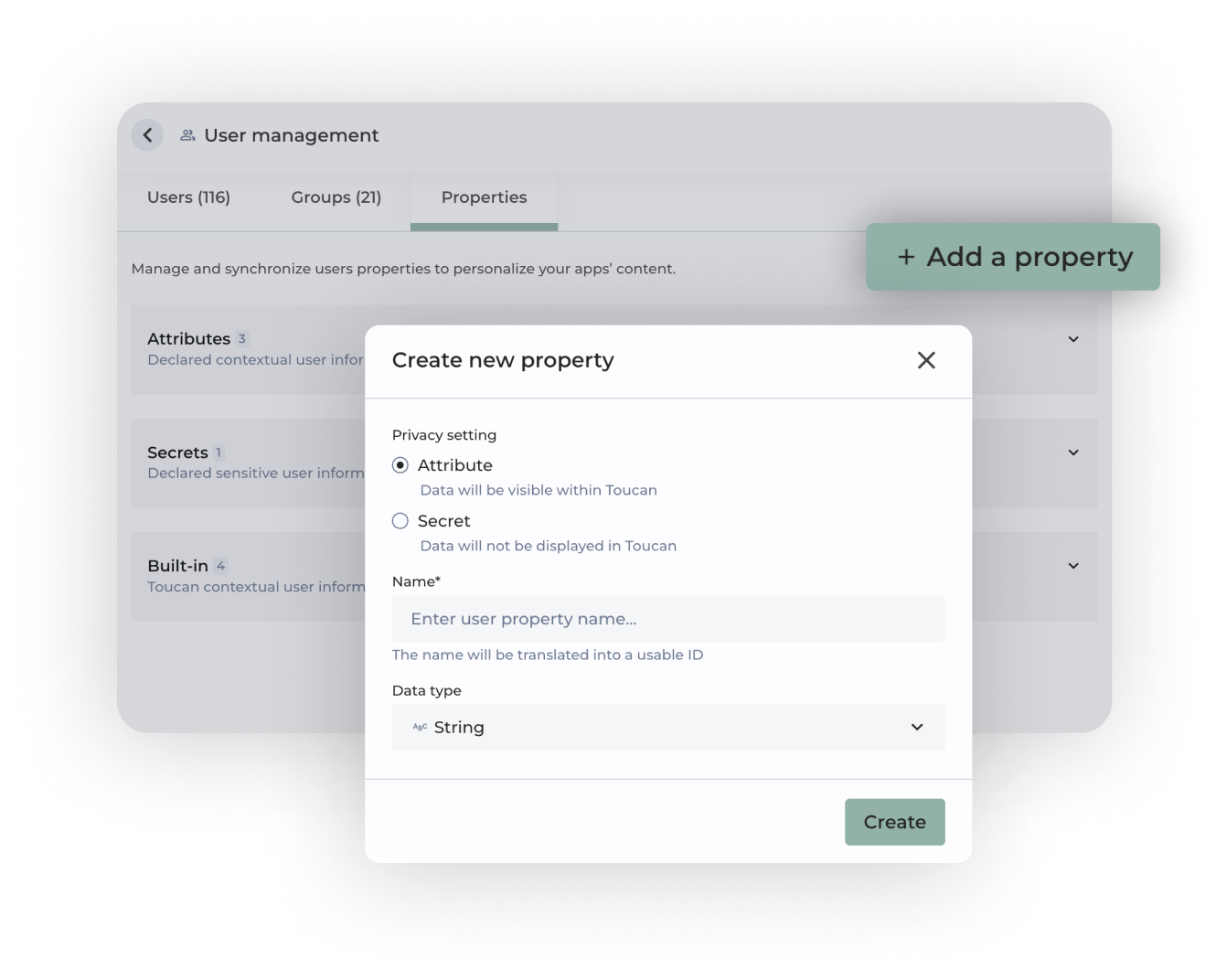
Secure your data
Ensure your data is protected with the highest standards. Our security measures not only keep your data safe but also provide peace of mind. Manage permissions effortlessly and maintain compliance with industry protocols, guaranteeing that your data remains safe and accessible only to authorized users.
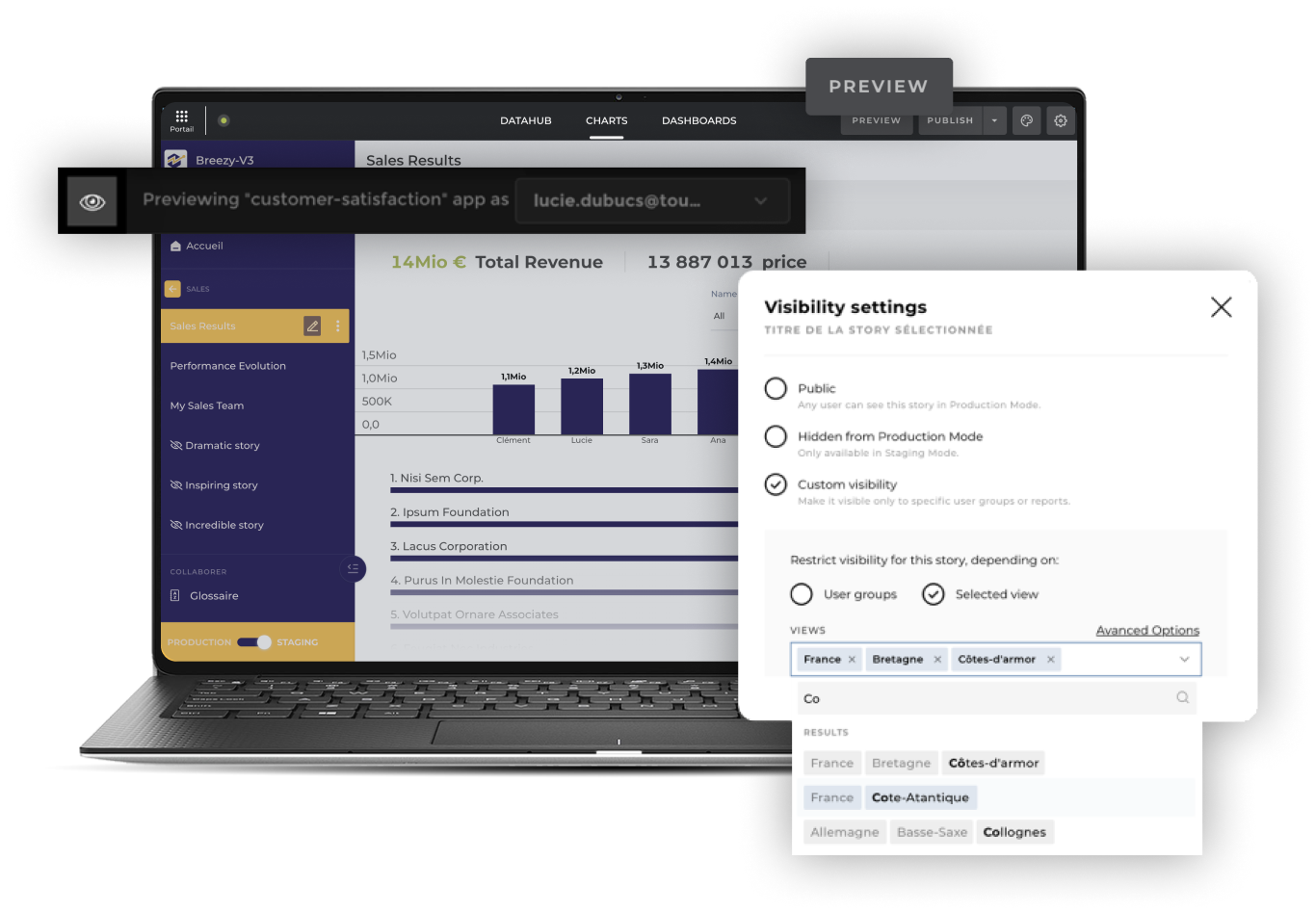
Effortless permission management
Set up security rules quickly at the app, role, user, and row levels. Our intuitive interface makes it easy to configure and manage permissions. Ensure that only the right people have access to your data without the headaches.
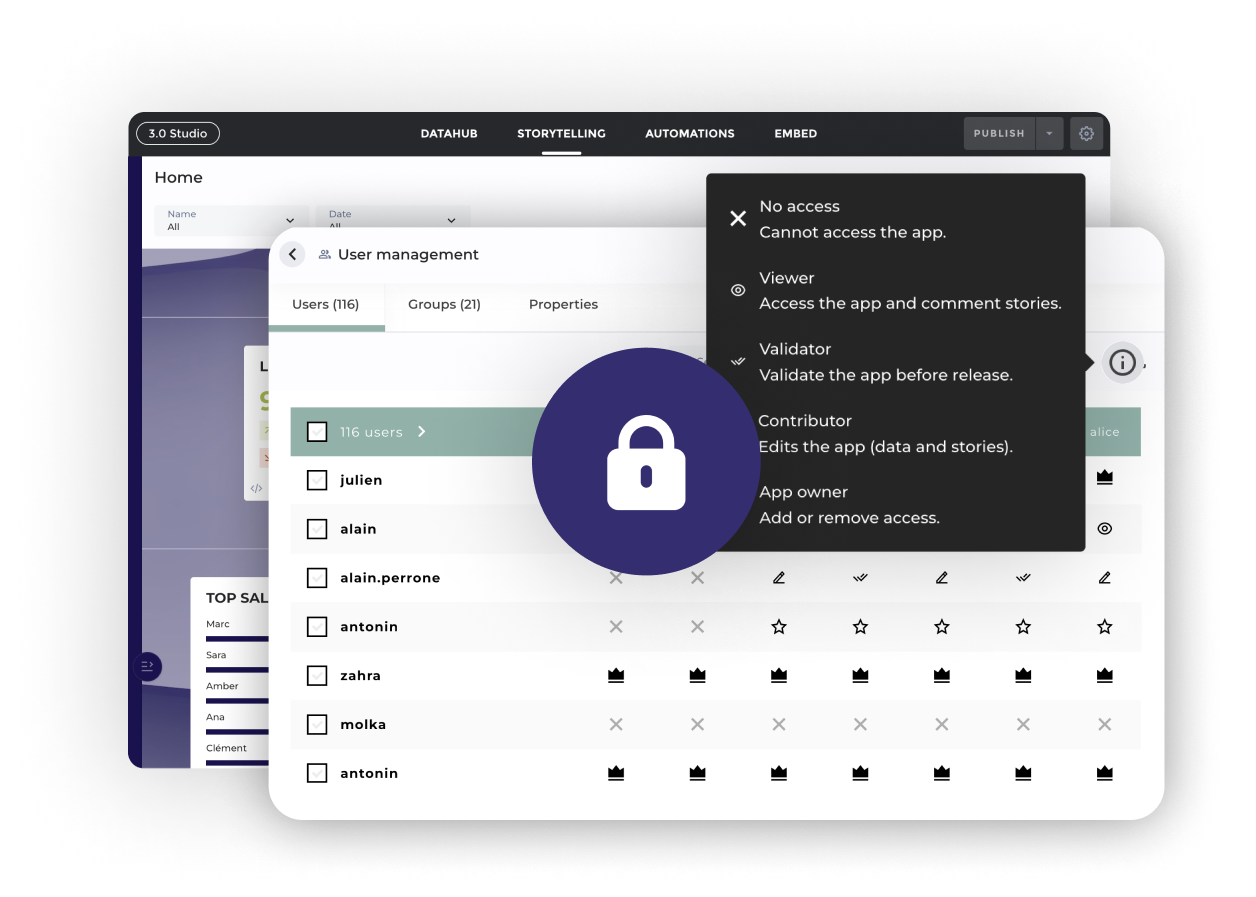
See what your users will see
With Toucan's "View As" feature, you can see exactly what a role or specific user will experience before deploying to production. The days of testing with fake users, roles, and passwords are over.
- Ensure permissions are set as intended without simulating scenarios or connections
- Test, adjust, and debug access rules in staging mode before deployment
- Reduce the risk of shared "test accounts"
Flexible authentication for any situation
.png)
When working with data, security is critical. But that doesn't mean you don't also need flexibility. We have both.
- Use industry-standard protocols such as SAMLv2 and OpenID connect
- Mix IdP sources to cover all your identification needs
- Combine multiple SSOs with local permissions databases
Flexible authentication for any situation
Prioritize data security without compromising on flexibility. Using industry-standard protocols like SAMLv2, OpenID Connect, RSA, and JWKS, we ensure secure authentication. With built-in SSO and the ability to mix IdP sources, all your identification needs are covered.
Our practices adhere to the NIST framework, safeguarding your data with advanced encryption and authentication.
Enhanced security simulation testing
Perfect your access rules before deploying with Toucan's "View As" feature. The built in stimulation allows you see exactly what a role or specific user will experience to ensure your security settings work as intended. Test and debug access rules in staging mode, eliminating the need for fake users and shared test accounts.
Cyber Security at Toucan
Toucan is committed to creating high-quality security.
Better understand our security and privacy management practices, as broken down within the 5 functions of the NIST framework. Find out how Toucan applies these Functions in its product.

Securely share your data without hassle
With comprehensive protection, you can focus on leveraging your data without worrying about unauthorized access.
Customer Stories


"Unbelievably impressed with how much Toucan allows us to modify. We have the ability to do anything we need to. It feels like an integrated component of our CSS."


"Toucan has cornered the market on customer service and without them, we wouldn't be where we are today."


"By narrating our insights, Toucan has helped the government reinforce the trust of our Citizens in the action of the States."

.webp)
"It took us less than 5 days to connect the data, build, and deploy our first analytics features inside our product."
LEARN MORE
Ready to get started? Experience data stories