Cyber Security at Toucan
The National Institute of Standards and Technology (NIST)
The National Institute of Standards and Technology (NIST) promotes and maintains measurement standards and guidance to help organizations assess risk. The main priorities of NIST were to establish a set of standards and practices to help organizations manage cybersecurity risk all while enabling business efficiency.
- The NIST Cybersecurity Framework is a voluntary framework that consists of standards, guidelines, and best practices to manage cybersecurity-related risks.
- The NIST Cybersecurity Framework is divided into five main parts or functions. Continue reading to learn how we apply these functions in the Toucan product.
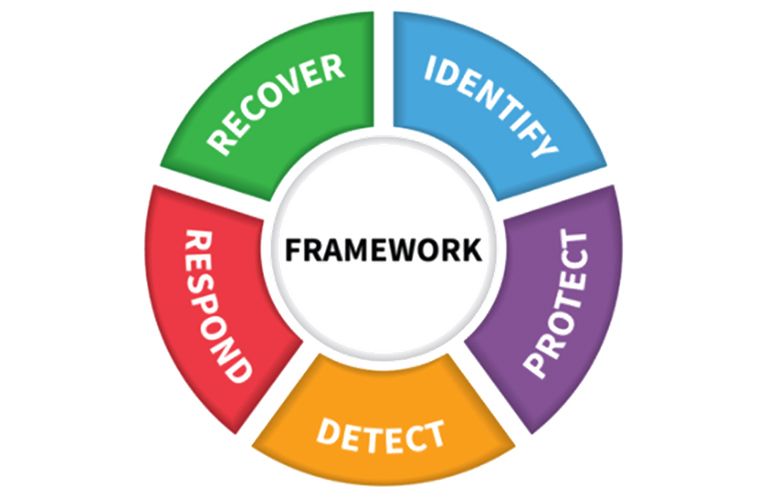
NIST Cyber Security Framework
At Toucan, all data provided by our customers is viewed as strictly confidential information. We work with companies of all sizes and industries around the globe and are committed to protecting and defending our customers on all security needs.
Implementing the industry-leading NIST practices, we follow a cyber security framework allowing us to meet security needs and present quality insurance around all our data security controls.
Identify
We manage cybersecurity risk by inventorying our:
- Assets
- Business environment
- Governance
- Supply chain
Protect
We ensure the delivery of critical services with:
- Awareness and training
- Data security
- Information Protection procedures
- Maintenance
- Protective technology
Detect
We identify cybersecurity events by:
- Detecting anomalies and events
- Applying continuous monitoring
- Applying cybersecurity detection processes
Respond
- Response planning communications
- Analysis after every event
- Mitigation of cybersecurity events